Phishing Awareness
“90% of all cyber attacks begin with phishing” – cisa.gov
Phishing emails are everywhere whether that be your work email or your personal. First thing first let me define a phishing emails. Phishing emails are emails designed to acquire sensitive data from the victim. Phishing emails can be made to look like big corps such as PayPal, amazon or even individuals you may know. In the section below I will show you where you might see the two different types of phishing emails.

Personal email are more likely to receive Phishing email that are pretending to be:
- Banks such as Chase, PNC, PayPal….
- Online shopping site such as Amazon, Walmart…
- Career sites such as LinkedIn, Indeed…

Work emails are more likely to receive phishing emails that are pretending to be individuals.(These are more advanced):
- IT support asking you to click a link randomly to reset password
- Higher management asking you to provide personal info or company private info
- Vendor asking you to click a suspicious looking link or Attachment.
Although the examples listed above are in two different categories, any example from above could make its way to your mail box.
Now that I have explained what a phishing email is and gave some context on where you might see them. Below we will see a more detailed analysis. I divide the analysis in a two tear approach.
Tear one: Grammar mistakes, free prizes, & using personal emails for professional matters.
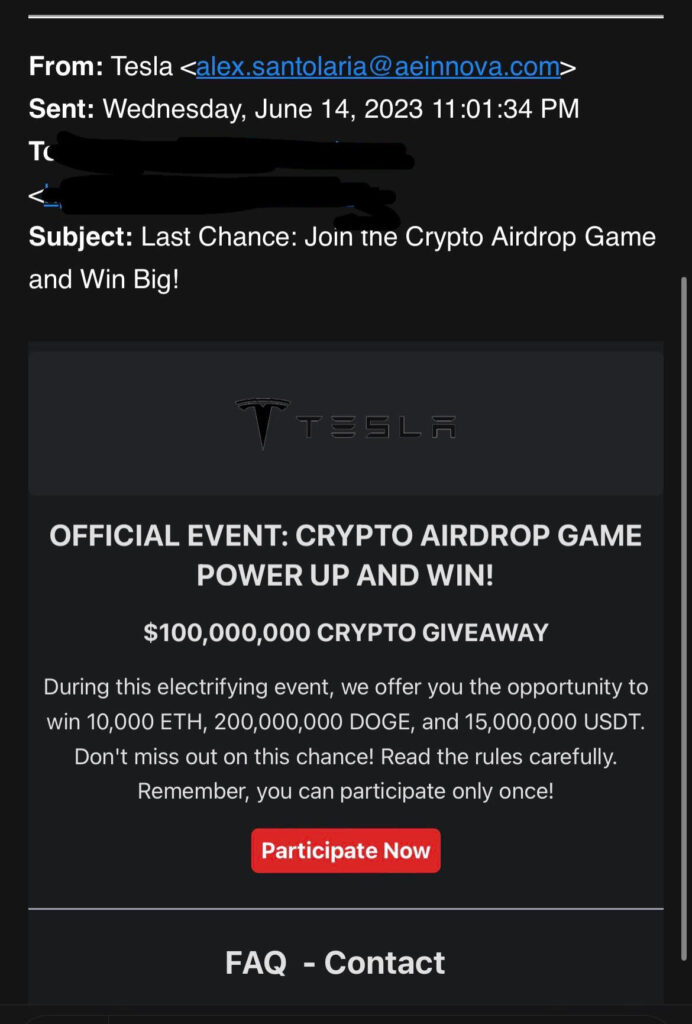
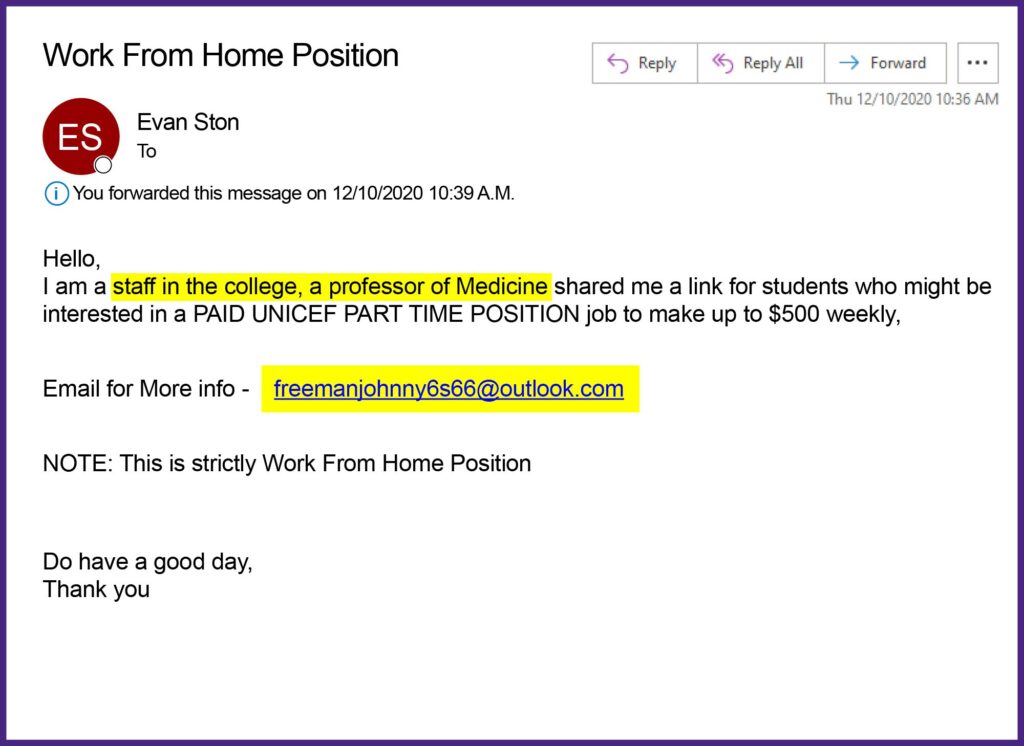
1. First being the Grammar, many phishing emails contain simple grammatical errors, these are a dead give away that a professional or company did not produce this email.
2. Another indicator is the use of Gmail, outlook, yahoo… emails in a professional setting such as Job offer or being contacted by amazon support or any situation where it is odd to use personal email.
3. Emails stating you have “Won free money” or Gift should also be considered suspicious immediately.
Tear two: Checking Root domain, reply to field, signed by field, and link redirection.
Understanding Domains:



Here i provide examples of some popular websites along with their popular sub domains. A sub domain is just an extension to a company. Using the examples above we have amazon music and google docs as extensions services that Google and Amazon offer. We want to keep this in mind when we view emails as threat actors take advantage of subdomains to pose as legitimate websites I will show example below on how.(This applies to both emails and website links.)
- Another thing to keep in mind is similar looking domains such as misspelled domains example: Amazan.com , PayPalsupport.com , or rneetup.com(r and n look like m).
- Another thing to keep in mind is different TLDs(.com, .net, .io, .xyz…) mixed with misspelled domains Example: Amazanhelp.support
- Subdomain trick is where threat actors use extensions example: Google.supportcorp.com, Amazon.freeasda.com. People tend to see a popular name and assume it is safe. (These apply to both emails and website links.)
Example of sub domain abuse and bad link
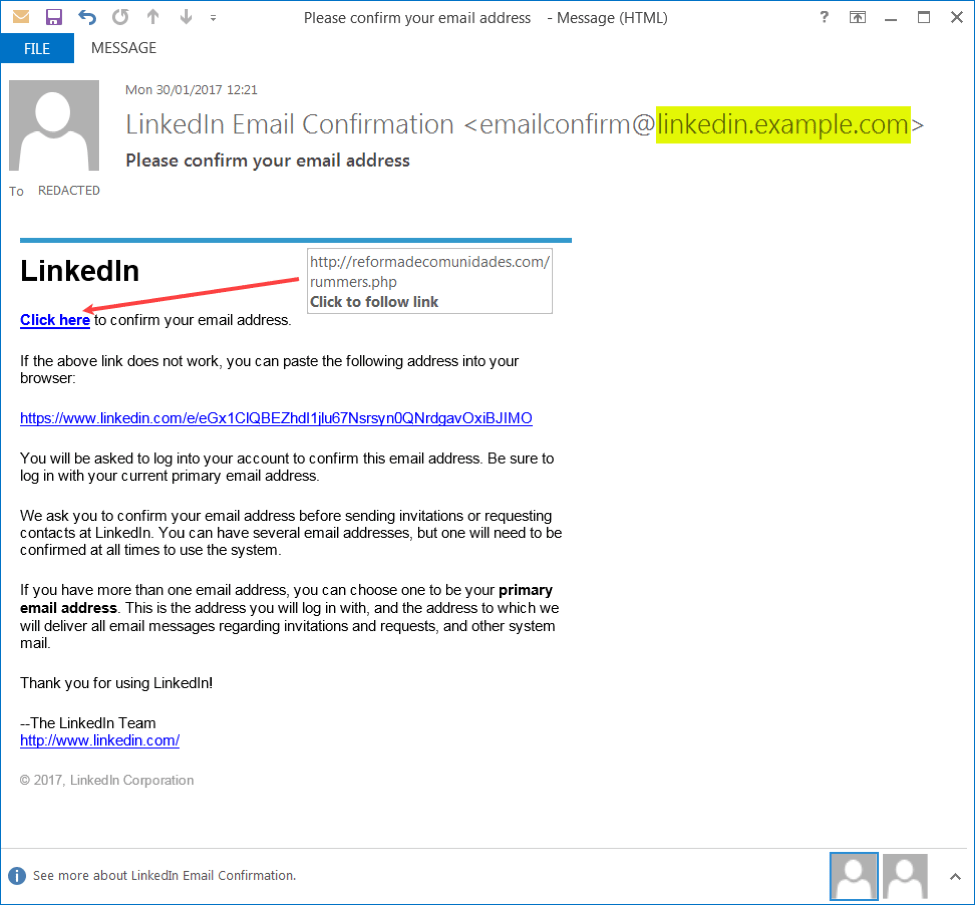
So here is an example of phishing email using sub domain to look like LinkedIn. As I mentioned above, right before the “.com” will be the domain and anything before that is considered sub domain( which can be anything). The Link pointed out in the picture shows that the link goes to another website. The actual link does not look anything like a linkedIn page as it show a different domain page as pointed out by the arrow.
Reply to:
The “reply to” field is what it sounds like- which email will the reply go to. This is important because even with visual tricks, threat actors tend to use personal emails and or a different looking email domain than the header.
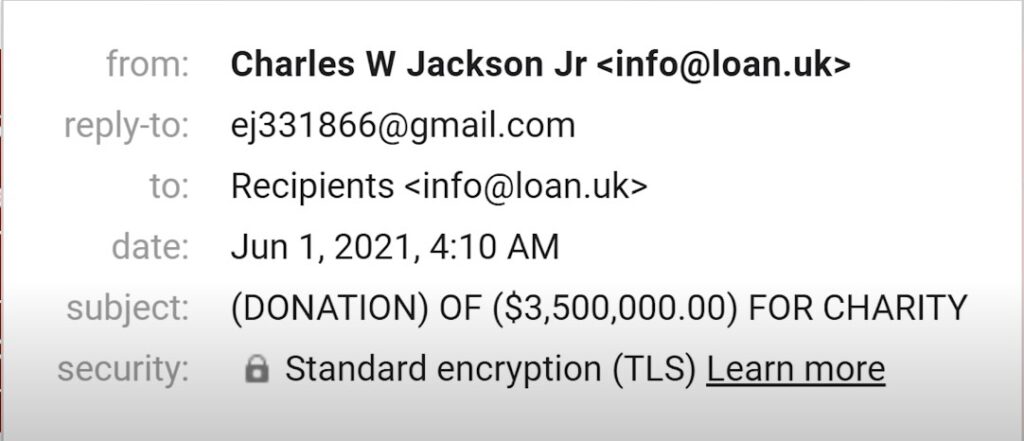
This example is using a more advance method of Spoofing where they take advantage of poor configuration on a legitimate companies email server(I’ll get more into that later) but never the less a personal email for the reply shows a miss match on who the email sender is pretending to be.
Signed by/mailed by (Via)
The via indication in the image below has a real world application as some companies use third party vendors to handle their subscription list(example marketing companies). But this also allows threat actors to send email using another companies domain as sometimes companies forgot to configure their SPF setting and this allows anyone to send email on their behalf but will show up as (Via “Company name”).
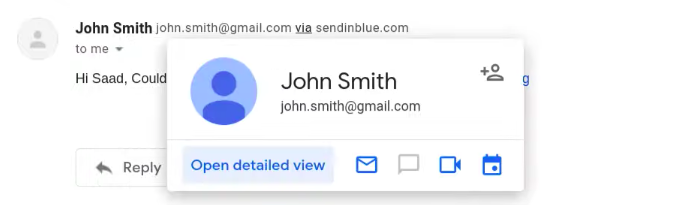
Above I show a example of a email being sent via a SMTP sever that is not the original. Sendinblue is a service that is used to host a SMPT server and like many of the threat actors they also too use their own to spoof but it tends to display on the side of the email.